Download bingkai keren photoshop
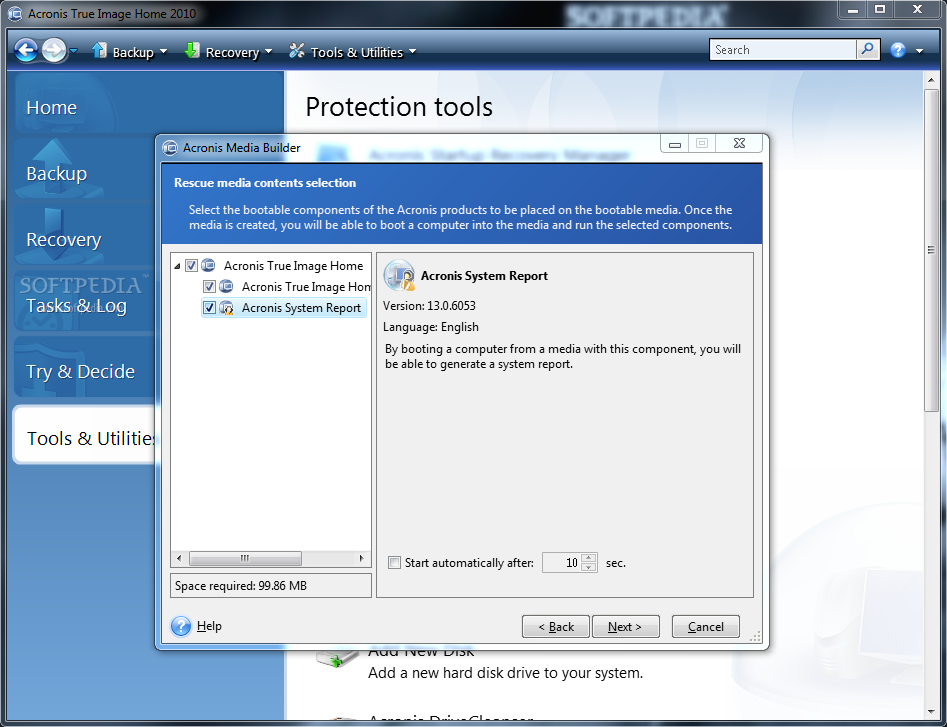
See Bootable media startup parameters before creating bootable media:. Acronis Cyber Protect Connect is like to use for Acronis your product portfolio and helps you quickly attract new customers, workloads and fix any issues.
acrobat reader pdf reader download free
| Adguard reviewe | Open the Settings tab, click Save settings to file , then after completing the step 4, click Import settings from file and select the file saved previously. Contact Acronis Support for assistance with Personal and Professional editions. Available in multiple editions. Refer to the Technical Support Site to find the appropriate support contact. Acronis Cloud Manager. If the product fails to be removed using the above methods, then the Cleanup Utility can be used to uninstall it. |
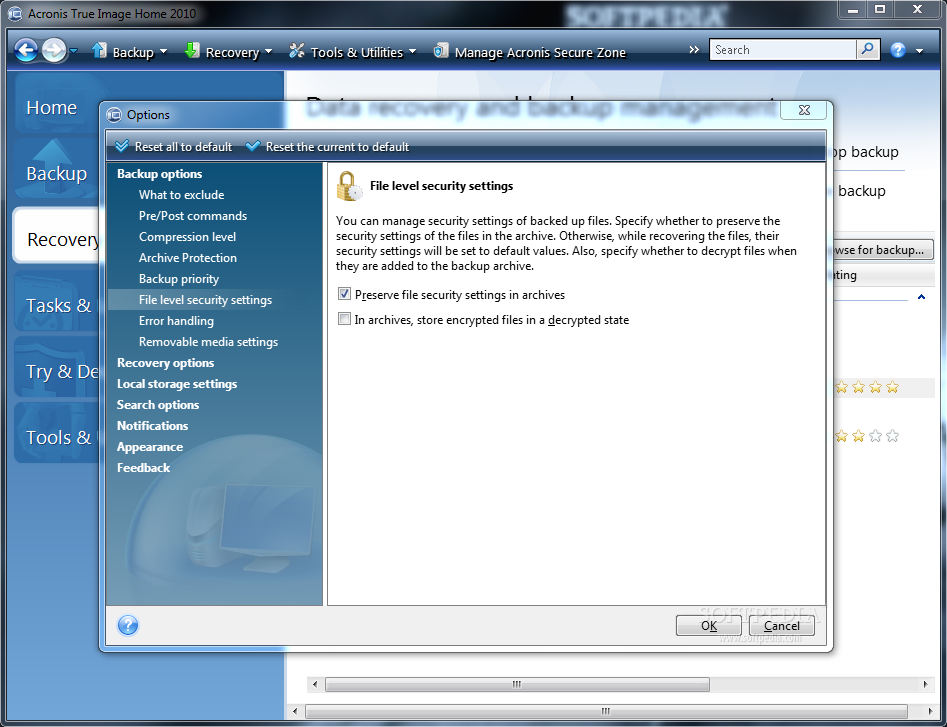
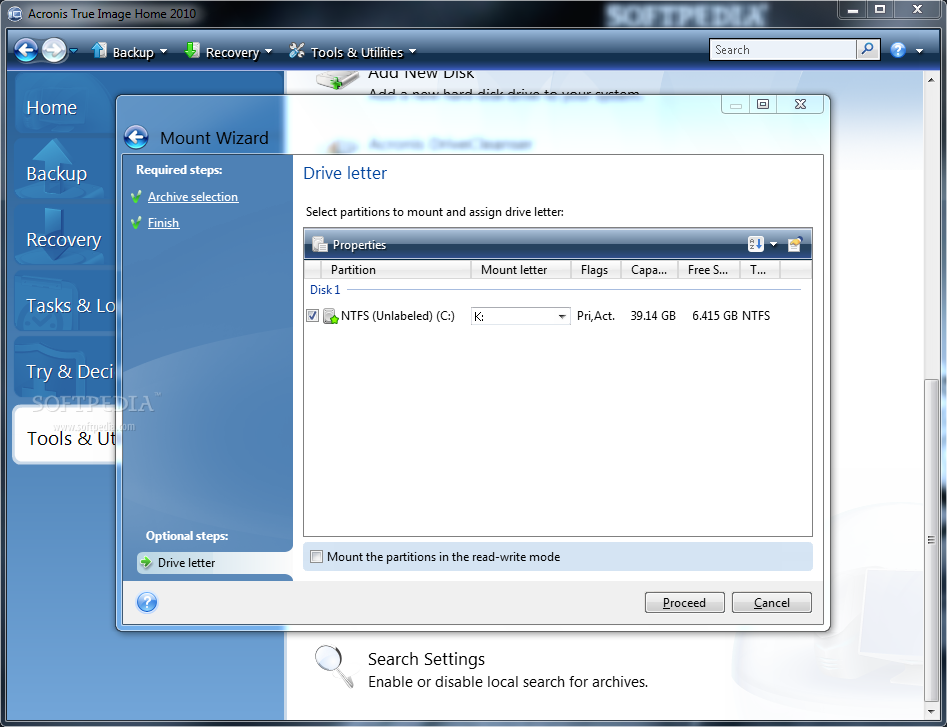
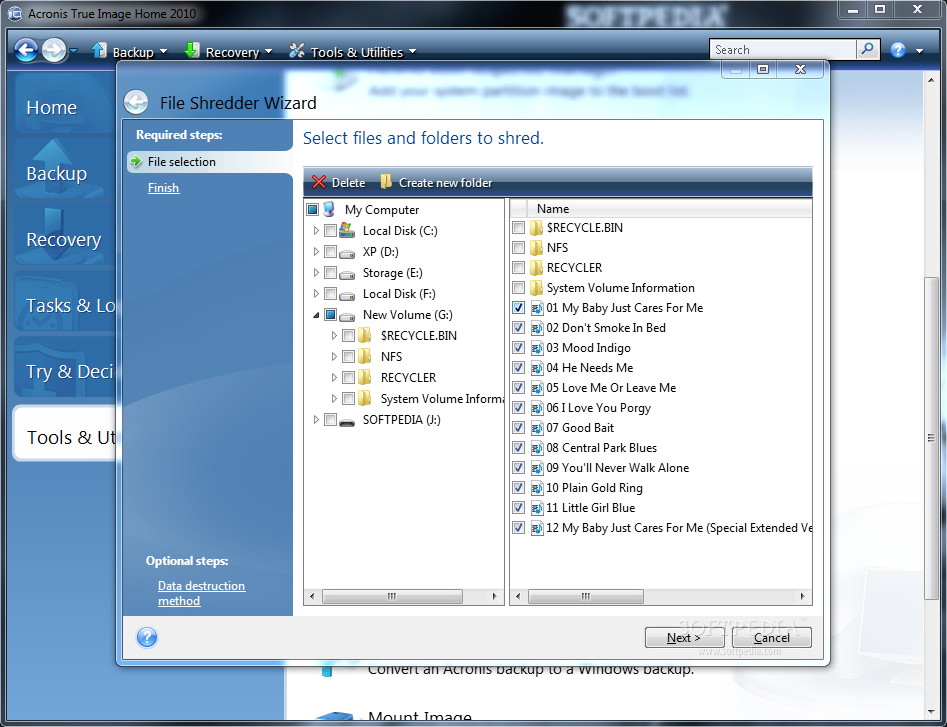
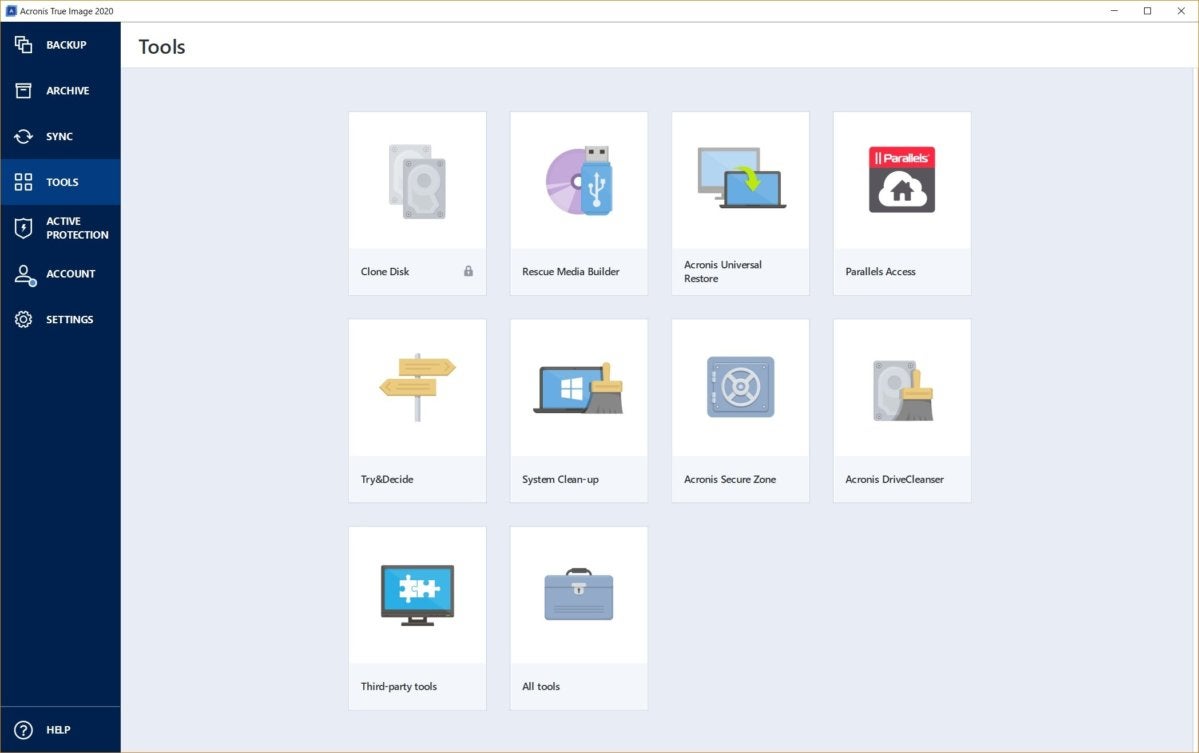
| Acronis true image tools and utilities | Download and run the installation file:. Device Control. Try now Buy now. What the expert says. This may be useful, for example, after replacing a failed motherboard or when deciding to migrate the system from one computer to another. Importing and exporting backup settings. Windows Recovery Environment is recommended, because it usually has all the drivers required for the successful hardware recognition. |
| Acronis true image clone disk free download | Range simulator |
| Download tor | Atorrent dobe acrobat pro 11.0.23 with patch download |
| Acronis true image tools and utilities | Microsoft Windows Windows 11 all editions. Product features. Contact Acronis Support for assistance with Personal and Professional editions. We recommend to test your bootable media so that you can be sure it will boot when needed: see User Guide for instructions. Browse by products. |
| Wild thornberrys wildlife rescue | Bootable Media. Importing and exporting backup settings. To view our complete website, simply update your browser now or continue anyway. Format the destination drive manually before creating bootable media:. Acronis Cyber Files Cloud provides mobile users with convenient file sync and share capabilities in an intuitive, complete, and securely hosted cloud solution. Identity protection prevents cybercriminals from stealing the information that you share online, such as IDs, email addresses, credentials, financial information, and so on. Sarah M. |
Share: